⭐ WordPress Malware Removal 2024

Are you suffering from malware infection in your WordPress site? In this updated WordPress malware removal 2024 guide you will learn about the process of identifying and steps to clean malware infection from a hacked WordPress site. This is meant to be an all-in-one malware removal guide, to find and remove malicious code in your WordPress website.
Removing malware from a hacked WordPress site is no easy task. It can lead to Google blacklist, website defacement and even screen of death issues.
In 2024, WordPress has been a prime target of cyber attacks. To secure your website, it’s recommended to conduct a complete security scan using a trusted plugin or with the assistance of a security professional. This scan will identify vulnerabilities and locate the source of any infections.
Table of Contents [TOC]
- ⭐ WordPress Malware Removal 2024
- ⭐ 10 Signs Your WordPress Site Is Infected With Malware
- ⭐ How to Detect Malware in WordPress Site?
- ⭐ Steps For WordPress Malware Removal 2024
- ✔️1 – Run An Antivirus Scan On Computer
- ✔️2 – Run Website Malware Scan Online
- ✔️3 – List Files By Modification Date
- 4 – Scan your downloads folder
- How to find and delete PHP files in a specific folder?
- ✔️5 – Back up your WordPress site completely and regularly
- ✔️6 – Deactivate Plugins/Clean Up WP Theme
- ✔️7 – Change Passwords
- ✔️8 – Find Malicious User
- ✔️9 – Remove the default ‘admin’ account
- ✔️10 – Lock WP Login To Limit Login Attempts in WordPress
- ✔️11 – Install Security Plugins
- ✔️12 – Change hosting provider
- ✔️13 – Restore Your Backup
- ✔️14 – Tell Google that We Are Clean
- Conclusion – Remove Malware from WordPress
- ?️ Get Started With WordPress Malware Removal Now
If you are trying to get rid of malware from your site, scan your site using WP Hacked Help malware scanner before installing any WordPress malware removal plugin. Also check out our Humungous list of vulnerability scanner tools 2024
During COVID-19, there has been a sudden spike in WordPress sites being infected with malware. Therefore, cleaning up a hacked site has become more important than ever. Once your site is hacked, Malicious codes can destroy your website, so it’s important to act quickly to remove malware from your WordPress site.
WordPress has become one of the most used tools worldwide when creating a web page thanks to the large number of templates and plugins that it provides, which allow practically anything to be done.
WordPress site security is not to be taken lightly. Being hacked can happen to anyone and these tips will help you to limit potential damage and Clean up hacked WordPress website.
Also Check Out Our – WordPress Malware Removal Checklist
⭐ 10 Signs Your WordPress Site Is Infected With Malware
There are several ways to check wordpress website for malware. We have an in-depth post here on how to check if wordpress site is hacked
The most important part to be protected against any type of threat is prevention, which means that we must take certain actions to remove malware from WordPress site and secure our website.
The main action that WordPress users should take is to always have their site updated with the latest stable version available, a new version usually fixes common WordPress Vulnerabilities detected in previous versions. In addition to this, it is also very important to do the same with the plugins we use, as well as eliminate all those that we do not use.
When a malware infects a site, there are many things that can happen. Among the problems that may appear are:
- Increase consumption of server resources, both web and MySQL
- Theft of personal data of users and customers
- Penalty by Google or Google Blacklisting
- Alert messages that your site is infected – “This Site May Be Hacked” Message in google
- Appearance of unwanted advertising
- Sending spam mail in bulk
- Disappearance of information from our site.
- It can compromise your website security and have negative impact on your SEO
- WordPress Ransomware
- WordPress Phishing attack
⭐ How to Detect Malware in WordPress Site?
The following steps provide a deeper understanding of the hack to identify malicious code in your website:
Make sure you check your backup for hacked files.
These files will have odd names and stand out from the other files in your WordPress install, or may have recent modified dates. If you open these files in a code editor like Dreamweaver, TextWrangler, BBEdit, Coda, etc., it is easy to spot something is wrong because of their color codes or the huge amount of code.
Perform Google Search
You can see if something is hacked by doing a Google search for related terms, this might be a div name in the code. In one of our client’s hacked site the file name was found to be ‘index.php’.
Check Raw Access Logs
To find out what files were compromised, examine the Raw Access Logs on your hosting cPanel. Look for POST statements in the log files and notice what IP address accessed them. This will give you a clue as to what exactly was compromised and when.
Obsolte/Outdated Plugins
Hacks are often the result of outdated plugins and themes. Look up which plugins you were using on your hacked site and see if it might have been compromised because of an older version. These can be plugins like Gravity Forms, Revolution Slider, timthumb.php script in a theme or plugin, etc. Hacks most often happen due to vulnerabilities that are known and easy for hackers to exploit.
Perform DB Scan
Search the database for illegal admin users and other hacked content. Wp Hacked Help provides you an AI Based WordPress malware scanner to scan your database for hidden malicious code. If you’re going to modify your database, back it up three times first!
DOWNLOAD NOW – WordPress Malware Removal Guide[PDF] at Open.edu – WordPress Malware Cleanup Steps (Infographic)
⭐ Steps For WordPress Malware Removal 2024
Easy Steps To Remove Malware From WordPress Site:
- Run An Antivirus Scan
- Run Website Malware Scan
- List Files By Modification Date
- Scan Downloads Folder
- Back up WordPress site
- Deactivate Plugins/Clean Up WP-Themes
- Change Passwords
- Find Malicious Code
- Remove Default ‘admin’ Account
- Lock WP Login
- Install Security Plugins
- Change Hosting Provider
- Restore Backup
- Request Google Security Review
Once we have realized that our site has been infected with some type of malicious code, the first thing we must do is to detect what type of malware has infected us and which files are the ones that are infected. Also, some useful steps to finding and removing malware from wordpress site. To achieve this goal, use the below mentioned steps.
✔️1 – Run An Antivirus Scan On Computer
Another option that we can use to detect files that have been infected is to use an antivirus that we have installed on our computer. With an FTP program, we can download the entire site so that each of the files that are part of the web is analyzed in search of malicious code.
Normally the antivirus is able to analyze the files while they are being downloaded, so once the download is completed we should only go to see the generated report to know which are those that have been designated as potentially dangerous.
✔️2 – Run Website Malware Scan Online
If the above options have not yielded good results or you do not like them, we can always use some of the online tools that we can find online and that are able to scan our site for malware. WP Hacked Help is among the most popular site which detects and remove malware from the WordPress.
Once our entire site has been analyzed, WP Hacked Help shows a report with the files that have been infected.
Within the online tools, we can also activate the Google Webmaster tool to consult its “Security problems” section where it will inform us about the type of threat we are suffering.
✔️3 – List Files By Modification Date
One of the fastest ways to detect potentially dangerous files is to access via FTP and sort them by modification date. Thus, in the first places will appear those who have suffered some type of change recently.
If we have not changed anything in them, it can be a symptom that inside there is some kind of code that is causing the problem.
The problem with this system is that you should go through all the folders that are part of the site to locate each of the infected files, a job that could be very tedious if the code has been inserted in a large number of files.
4 – Scan your downloads folder

You must scan the download folder for possible malware. Typically, the download folder does not contain any PHP files. So, delete all PHP files in a wp-content folder.
Now, you may be wondering how to find all the possible PHP files in this folder because the size of your download folder is much larger.
How to find and delete PHP files in a specific folder?
- Using the cPanel File Manager

You can do this with the cPanel file manager. Type .php in a search bar and select the current directory. The file manager will display all PHP files.
FileZilla does a great job if you want to filter a specific file type and only want to delete certain types of bulk files. Here’s how to use the FileZilla file filter;
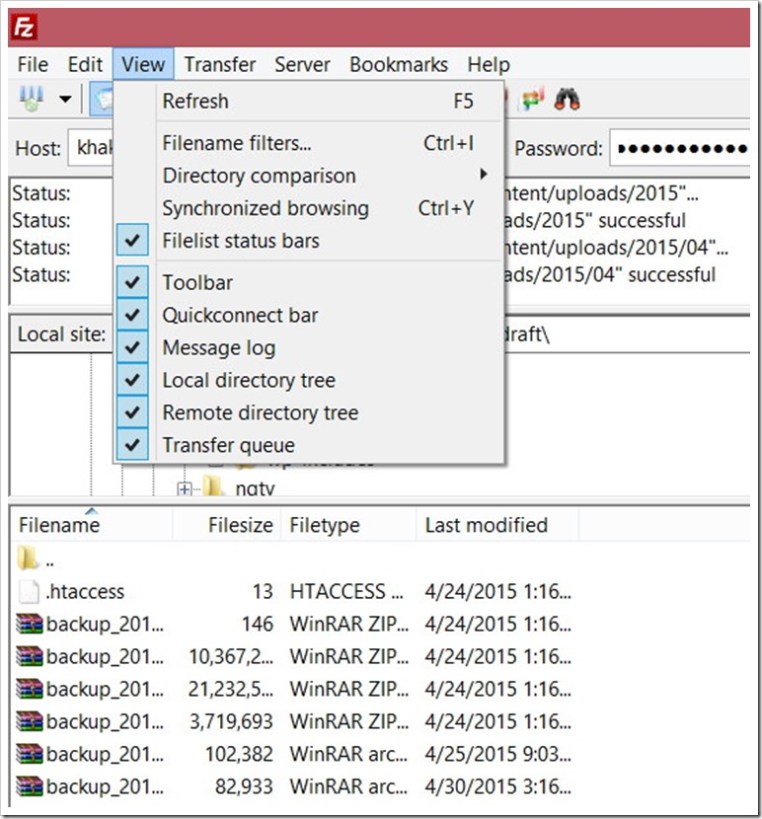

Another way to discover PHP files in the download folder is to use Windows Search. Download the “uploads” folder on the PC and use the Windows Explorer search to list the PHP files.
After cleaning your wp-content folder and reinstalling the theme and plugins, also install a security plug-in named Anti-Malware and Brute-Force Security, then analyze your WordPress with this plugin. This plugin can detect many known threats and traps and correct them. It can also update your obsolete Tim thumb script.
✔️5 – Back up your WordPress site completely and regularly
Before any intervention, make a regular backup of your WordPress site. You must save the following items:
- Your MySQL database
- Your FTP account
Your host may have a full backup system directly accessible via cPanel for example. Take the opportunity to get a complete ZIP of your site!
Also read – How To Export WordPress Database with Phpmyadmin
✔️6 – Deactivate Plugins/Clean Up WP Theme
The most likely way that WordPress has hacked is that it’s a plugin or theme and a vulnerability that it had. Or you have downloaded free of charge from unreliable sources.
The step we are now going to take is simple but much more important in order to remove malicious code:
- We must Scan & Detect Malware in WordPress Themes and make sure we download themes from the original source and replace the files in the folder with the name of the template in /wp-content/themes/ by the newly downloaded.
- If you made any changes directly to these files and did not use a child theme, you will lose those changes.
- If so, you will have learned how important it is to create and what the child theme is for.
- The next step is to repeat what we have done so far but with the folders that contain the plugins. We will have to download the clean plugins from their respective repositories and replace them.
- That is, delete the path /wp-content/plugins/ the folder of each of the plugins and copy the new files.
✔️7 – Change Passwords
An important measure that you must take is to change all the passwords that have relation with your web.
- Change the password of all users with administrator level.
- Change the access password to your hosting panel.
- Even if you do not make much use of FTP, change the password.
- And finally, change the password of the user of the database.
The last two steps you can do from CPanel or from the panel that you from your hosting provider in your case:
- If you use CPanel you will have to go to the Database section-> MySQL Databases-> Current Users-> Change password.
- Once you have changed it, it is important that you update it in the wp-config.php because otherwise, the web will not work when not connecting to the database.
Open the file and in this line, change the password:
/** MySQL database password */ define( 'DB_PASSWORD', 'password_here' );
And take the opportunity to review this file looking for any line or text that is suspicious. It may also be the case that it has to modify it.
Use secure password whether on your WordPress site or on your personal computer, must have a password of at least 8 characters including:
- Numbers ;
- Special symbols;
This will save you from hacker attacks of testing dictionary words.
- Avoid any information that refers to your personal life such as a birth date, a department number. Nowadays, privacy is poorly protected on the Internet.
- Of course, use unique passwords for your different accounts. A password to govern them all and we have seen how it ends.
✔️8 – Find Malicious User
If you are registered and your WordPress website has many users, click here. Some hackers register on your WordPress and execute malicious scripts exploiting any vulnerability of their theme or their plugin. You can use Stop Spammers to spam and delete them.
✔️9 – Remove the default ‘admin’ account
In older versions of WordPress, the admin id was the administrator account created during installation. It is, therefore, a first-rate identifier tested by hackers during brute force hacking attempts. (Also Read – How To Change Your WordPress Username)
Limit the risks by watching this video podcast to learn how to remove the WordPress admin account if your installation is old.
✔️10 – Lock WP Login To Limit Login Attempts in WordPress
By default, it is possible to test as many login/password pairs as you want to connect to your WordPress administration. Login LockDown records the IP address and timestamp of every failed WordPress login attempt. After a certain number of attempts are detected within a short period of time from same IP range, then the login function is disabled. This helps to prevent brute force password discovery and protect your wordpress from brute force attack.
So install the Login Lock Down plugin to restrict the number of attempts allowed for a certain amount of time.

Upon activation, you need to visit Settings » Login LockDown page to configure the plugin settings.
For more security you can also use Setup WordPress Two-Factor Authentication
✔️11 – Install Security Plugins
Installing security plugins that can detect and prevent common vulnerabilities, such as WordPress SSRF exploits, is crucial in protecting your WordPress site from malware. These plugins can identify and block malicious requests in real-time, preventing them from exploiting vulnerabilities in your website’s code.
There are both free and paid options available, and we’ve included some of the most popular and reliable WordPress security plugins that offer real-time detection.
✔️12 – Change hosting provider

Maybe after all this journey of disinfection of your WordPress, the time has come to consider changing hosting. Contact your hosting provider first, if they cannot help you further in this regard then get a new more reliable hosting with better customer service.
Indeed it is not true that the infection of your website has arrived due to the security of hosting, far from it. But everything adds up and a good server with well-established security measures is important.
Also Read – “This Account Has Been Suspended” – WordPress Down [Fix]
✔️13 – Restore Your Backup

The most recommended method is to restore the site from your backup. Even if you have customised the theme, these backup files will help you retain your customisation. Install the recovery plugin and remember that to recover the site from a backup, use the same plugin that was used to back up your site and re-scan the entire website with our WordPress malware scanner.
✔️14 – Tell Google that We Are Clean

If your website was hacked and showed the notice we saw at the beginning, it is because Google had detected it and had put the “infected poster.”
This can be seen if you access Search Console, from the Security Problems menu.
Once you have cleaned up all traces of malware we can ask Google to reconsider the website using the Request a Review tool that you will see in the same previous menu next to the warning that your website contains malicious software.
You should describe a small report of the measures you have taken and how you have solved the hack and send it. Wait to check your website and you will be informed via email of the result.
If everything has been done well there should be no problem to remove google Blacklist Warnings.
Conclusion – Remove Malware from WordPress
As you may have seen, recovering a Hacked WordPress site that has been compromised and infected with some malicious code injection is not entirely complicated.
You will have to be patient and be careful with all the WordPress malware removal steps explained until you get to have your website clean and operational again.
It is true that the infection may have gone a step further and have the code database injected. In this case, the recovery is more complicated because one would have to look for certain patterns that are used as malicious code, among all the tables.
And it is also true that sometimes with these steps may not reach a complete cleaning and would have to get more artillery and a magnifying glass deeper to find where the problem.
But in general, the usual WordPress hacks such as:
- WordPress XSS Attack
- Web Shell PHP Exploit
- WordPress Arbitrary File Deletion Vulnerability
- WordPress Pharma Hack
- WordPress .htaccess hack
- WordPress DDoS Attack
- WordPress Malware Redirect
- Japanese Keywords Hack
- WordPress SSRF Vulnerabilities
are usually solved with these cleaning guidelines.
We do not want to end without commenting again on the importance of taking precautions from the beginning with security measures, through plugins, good server and common sense with passwords. And it would not hurt if you decide to hire WordPress security services offered by by WP professionals.

?️ Get Started With WordPress Malware Removal Now
Our WordPress security services includes malware removal, hack recovery, hardening, WordPress updates and more.

![How To Remove Malware From Hacked WordPress Site [2024]](https://i0.wp.com/secure.wphackedhelp.com/blog/wp-content/uploads/2018/12/How-To-Remove-Malware-From-WordPress.jpg?resize=381%2C300&ssl=1)

