
This Site May Be Hacked Warning in Google
Table of Contents [TOC]
WordPress, by default, is a fairly secure content manager, and together with protection features, and security layers that add many free plugins, it is further reinforced. However, bad practices or add-on vulnerabilities can compromise it and leave it easy prey for hackers. But the worst, still, is not knowing that your WordPress website is hacked until it is too late.
Google noticed an 180% increase in the number of hacked websites over the past year. In other words, it’s your own computer or device (phone or tablet) that displays the warning “This Site May Be Hacked” message which means your site has been infected with malicious code.
Through this message, Google protects you from possible virus infections by preventing you from accessing them. This doesnt means the google search results are hacked(some people may think this), but your own site is hacked 🙂
Therefore, today, we will give you a set of symptoms that warn you that your website is intervened and how to remove “This Site May Be Hacked” message in Google search for wordpress site, in this detailed GUIDE. Have a cup of coffee at hand!!
As we have said, the WordPress kernel package is a fairly compact and robust security-level system, and every time a security vulnerability or error is discovered, a smaller version is quickly released that resolves it in record time.
However, this does not mean that your website free of security problems, so we use plugins to improve this aspect. However, what characterizes “professional” hackers is that they sneak in, and without making much noise.
It is a very arduous task to check if your WordPress website is hacked or not, since several forms of attack that compromise the security of your website, have no visible symptoms or signs, and there are no blunt and reliable tools that assure you emphatically “Your website is infected or clean”.
However, there are some measures you can take periodically, which can give you a general idea of the overall state of your WordPress website.
Also Read:
- How to Fix “The site ahead contains harmful programs”
- How To Fix ‘Deceptive Site Ahead’ Malware Warning?
This Site May Be Hacked – Warning in Google

Well, as we all know that Google is the most popular Search engine out there. As a result, Google has a responsibility of keeping its users safe. For a while, Google has been working hard to warn people who visit potentially safe websites.
You’ll see the “This site may be hacked” message in google search results for your wordpress site, when google believes that a hacker might have injected your site with a malware or it comes across any suspicious redirect or cloaking on your WordPress site. some of the existing pages on your site might have been injected with a spam or infected by any kind of WordPress hack such as malware redirect, Pharma Hack, eval (base64_decode Hack, Japanese Keyword Hack or Gibberish Keywords…..
The primary criteria that Google uses to determine whether a site is secure is its use of HTTP over HTTPS. A site using the old one will be penalized by a warning like “This site may be hacked“.
Google examines billions of URLs daily for malware, spam, hack, etc. It then flags the ones that might have been compromised.
Google classifies compromised websites into two broad categories:
- Attack sites: Websites that host software capable of damaging the visitor’s computer. Google marks such sites with the warning “This website may harm your computer“.
- Compromised sites: Websites that might be hosting spam content or malicious code added by a hacker. Such websites appear in Google flagged with “This site may be hacked“ warning.
If Google tells you that your website is not secure, you will definitely need to do something. Moreover, the visitor traffic to flagged sites is restricted until the issues are resolved. This warning proves to be a serious loss for your business as you are losing potential customers every minute.
How To find out that your Website is hacked
This is the first premise that you have to be clear. Most hosting providers will simply disregard the matter, and will simply drop the web if they detect it.
Everything you can do to recover your website is up to you. What you know to do, or why you hire a professional to do it for you.
In very few cases your hosting will get to find out what happened and discard your website. What usually happens is that they leave it offline until you prove that it is solved.
If you contact Google, they will tell you the right solutions, and contact them to review the site again, and to remove malware warnings from your website which is a big red splash page with “This site may be hacked” message next to your site in Google’s search.
At most articles, what you get is a generic list of actions to take, but that will not work for you, because they are not adapted to WordPress.
And one false step and you will end up deleting your entire site or your database. And it is not what we really want?
The first thing is to detect that you have WordPress hacked
Well, yes, obviously it is the first thing you have to know.
But if you manage to detect if your WordPress was infected by malware in time, you will have a lot of wins, before more damage occurs.
And today, there are plugins and or online malware scanners available to detect if you are infected.
But let’s get to the “heart” of the matter. What are the ways to find out that your website with WordPress is infected?
Site Health Checkup
WP Hacked Help scanner is an online tool which is one of the best WordPress security services. It offers a thorough check of your website for malicious code, spam injection, website modification, and more.
It also checks your website on several, tools, including Google Safe Browsing and other malware blacklists to make sure your domain is clean. The WP Hacked Help tool does not only analyze the URL you enter but also explores the other linked pages to provide a quick and complete analysis.
It checks your website for known vulnerabilities and suspicious code. It has a system to maintain an index of vulnerabilities detected by their system and check your website for these security leaks.
It also tries to detect your version of WordPress, installed plugins and robots.txt files. After the analysis, the results are presented in an easy to understand format with the explanation of each element.
Google Safe Browsing
The tool secure browsing Google lets you know if a URL is considered dangerous by Google. Google monitors billions of URLs, and if it suspects that a website is distributing malware, it considers it dangerous to view them.
This could potentially damage the reputation of your website because users from Google Search or Google Chrome will receive a warning page when they visit your website. If you use Google Search Console, you will be notified when your website is marked as dangerous with instructions for the warning to be removed.
Why didn’t you know that Google Chrome is one of the best to detect malware? Much better than more expensive software.
If before you made the detour to page 503.php, you browsed through your website, you could already receive infection notices. That will give you the first clue about where to start cleaning.
Another option is to verify the scans that Google made of your Web, to see what malicious files it detected. To do this, visit http://www.google.com/safebrowsing/diagnostic?site= yourdomain.com
And remember to replace yourdomain.com, with the URL of your website.
Here you can see where the malicious code is hosted, so these sites have been inserted into your code without finding out by hackers.
You need to find these links and remove them from your files. Normally you will find them in the files of your theme, which is where hackers usually put it.
On other occasions, you will see that they have uploaded their own files, which are not part of your theme or WordPress, and link to them. In these cases it will be useful to have the original files of the theme, if you have not modified anything, you can delete everything and upload it again, or save only the modifications.
Google Webmaster Tools to detect incidents and malware
In Google Webmasters Tools, go to the domain you want to review and click on “Security Issues.” You will have a detail of what Google has indexed.
Domain Name System (DNS): You can find out if your domain name and hosting space are well connected and configured.
Server Connectivity: Google notifies you if the server is available and responds correctly to connection requests.
Exploring the robots.txt file: Google and the other search engines analyze a text file at the root of the main directory of your blog. This file lists the permissions to crawl your blog by search engines and normally for other robots. It’s still theoretical. Who tells you that all robots take it into account? 😉
You will be able to see if some URLs pose concern (dead links, links not followed by Google, an error of redirection and more)
Use Fetch as Google Tool
Use Fetch as Google, and verify that the page appears the same to Google as it does to a user. If it doesn’t, that is considered cloaking, which is a violation of google guidelines.
Use a Monitoring Service that Includes Site Changes
The use of monitoring Services for a website is important, surely you have heard it more than once. It is relevant because it is one of the factors that Google considers when it comes to natural positioning in the search engine. It is also an element that is part of the Quality Score, the quality score that Google gives to the page and that influences the price you will pay when a user clicks on your Adwords ad.
Such monitoring services improve the user experience, understood as all those factors linked to the interaction of a user that affects their perception of the web. It deals with elements such as the user’s emotional behavior while browsing. A slow loading web influences the experience and feelings in a negative way and will drive away the conversion we expect. In addition, a negative experience increases site abandonment and increases the bounce rate, another factor that influences SEO.
Google’s free tool displays charging time and offers recommendations to improve performance. Good practice suggestions include factors from uploading images and files to recommendations on how to reduce the number of HTTP requests.
Grants a score of 0 to 100 for web and mobile-based on total web optimizations, not just speed.
A tool that provides a diagnosis on the overall performance of the web and shows a speed test. Determine which elements of the page are the slowest to load. Monitor sites and servers on the Internet and alert if problems are detected.
A complete tool that analyzes the web in depth and creates detailed reports on the origin of the problems. Detects poor server settings and shows which external scripts slow down the web.
It has a free and paid version.
- Dareboost
For those who need a visual tool that shows the data in detail in a simple environment.
Dareboost manages web performance with functions beyond speed, such as monitoring, analysis and benchmarking. Check more than 100 improvement practices mention common mistakes on the website with a comprehensive audit report on performance, SEO, accessibility, and security.
The main features offered by WPHH are the control of the files uploaded to the WordPress website, the management of a blacklist of control, security notifications, etc.
 There is malware analysis, even remotely with the scanner. It also offers powerful protection from various vulnerabilities for the website that can be obtained and activated to make your website much safer.
There is malware analysis, even remotely with the scanner. It also offers powerful protection from various vulnerabilities for the website that can be obtained and activated to make your website much safer.
How to Remove Google’s THIS SITE MAY BE HACKED message?
Now that we know the ways to find out that your Website is hacked, let’s know how to remove this site may be hacked in WordPress. In general, it is always advisable to make a backup copy of your WordPress website before trying these types of procedures, in case something goes wrong. When the backup is ready, you can start working on the error.
As we mentioned earlier, this error can be caused by a breach in the security of your site. This is one of the reasons why the message may continue to appear even after the threat has been removed. This is because the hacker has found what is commonly known as a backdoor, which means “security breach” and can be used by the hacker. This vulnerability can be caused by a stolen password, incorrect permissions, or others.
We have identified the website is hacked. Next, we will show you how to fix “This site may be hacked” warning.
The first thing to do is keep calm and pay attention to the different alternatives that we will show you step by step in this guide on how to fix a hacked WordPress site.
Here’s what you’ll need:
- FTP Access to your website.
- A Google Search Console Account.
- A web developer that can clean up malicious files and scripts.
Have a professional do it for you
If we have no experience with servers and do not handle codes, it is better for a professional to repair our website. This as the first step.
The explanation is very simple, hackers leave Backdoors in the form of scripts in different places of our site. This allows them to return to the crime scene as many times as they wish.
Although we will teach you some techniques to find those doors and eliminate them, any website owner will be more relaxed if he hires a security expert who performs the correct cleaning of the website. Of course, this specialist will charge for doing so from $ 100 to $ 200 per hour, which is expensive for a small business owner.
If we do not know about technology or have time to solve the hacking problems of our website, then it is preferable to leave it to a specialist for greater peace of mind.
If instead, you are a DIY user (do it yourself), then you must follow the steps below to recover your hacked website and remove this site is hacked message from search results.
Initially, consult with your hosting company
In these cases, most web providers are very useful. They have specialists dedicated to solving this type of problem every day. They are knowledgeable of their own hosting systems, which will serve to guide us more effectively. So the first thing we will do is get in touch with them and follow their instructions.
It is likely that the problem is not affecting only our site, moreover, if it is a shared type of hosting.
Our hosting provider can also inform us about the type of hack, its origin and location of back doors, among other things.
Verification is the very first step in the removal process. It basically means to prove that you own the site that you claim to own. You can verify your site on Google Search Console. They have several methods of verification like meta tag, HTML tag, and Google Analytics Tool.
To check unauthorized ownership, go to property owner management page. Make a list of unauthorized users and delete them. Don’t forget to remove all meta tag and HTML files that were used to verify the ownership of the unauthorized user.
Restoration of previous WP backup
We can restore our website, from an earlier point (before the hack), if we have made a backup recently. This is the time when we can say that frequent backups are worth gold.
However, if our website is one of those that constantly change the content in one day, we are likely to lose an important part of our information, although not all. In these cases, we must analyze the pros and cons to modify the frequency of backups.
Suggested Read – How to Backup WordPress Database Manually & With Plugins?
Search for hidden administrators on your website
Verify that users have administrator privileges but do not recognize them. There must not be many!
Those you find, eliminate them. For more info read: How to remove hidden admin users on your website?
Scan for malware and identify vulnerabilities & backdoors
Run a WordPress malware scan to make sure that the site is free from any malware or content that the hackers might have left behind. Remove all infected files and patch all back doors.
To begin, we must eliminate those inactive WordPress themes and plugins that we are not using or are inactive. It is in these themes and plugins where hackers hide their back doors.
A WordPress Backdoor is the means by which a stranger evades entries for authentication to remotely access the server without being detected. In general, hackers begin their attack by finding the common wordpress vulnerabilities in the first place, one or more illegal back doors.
The biggest problem when you are infected, is that hackers place backdoors to ensure access to your website again. You have to check every WordPress file, plugins and scan WordPress theme for malware.
That is why you will see that we have been telling you the folders that you can delete and replace directly with a clean installation. Do it with all plugins and themes, and you’ll close all the back doors!
Now you have files that you have modified by hand, and they are in your backup. You have to upload them again to your server, scan them before with an antivirus .
Scan your site using WP hacked help wordpress security scanner. It will tell you what are the hacks and their locations that infect our site. WP hacked help provides complete 360° WordPress malware removal & scanning solution. It provides great features like automatic daily scans, access log reports, vulnerability assessment, etc. It also provides an option to schedule regular scanning.
The most commonly used hiding places in sites are plugin themes and directories, file upload directories, wp-config.php, wp-directory, and .htaccess files.
We will have two alternatives to solve this hack problem. We manually delete the found code or replace it with the original file.
As an example, in the case that the hacker has modified our main WordPress files, we must upload new files from a new download or all of the files so that we can eliminate the affected files.
We must ensure that the names of the theme folders and plugins match the original names. Hackers usually add files with names similar to those already existing and that we are used to “passing them by.” It’s easy to ignore them: hell0.php for hello.php, adm1n.php for admin.php, for example.
We recommend continuing to insist on this step until the hack or hacks have completely disappeared. This method allows them to recover access even after we have found and removed any of the plugins or themes used by them.
Carefully verify user permissions
Let’s look in the user’s section of our WordPress to verify that only we, and our trusted team, have access as website administrators.
In case of finding any intruder or suspect, we should delete them immediately.
Modify your secret keys
As of version 3.1, WordPress generates encrypted security keys. If a user entered with a stolen password is registered through cookies. To repair this, we must disable cookies and create a new set of secret keys. It is required to generate new security keys and add them to our wp-config.php file.
Check directories for malicious files on your server
Download a clean copy of the latest available WordPress that you were using on your website. If you are cautious, you will be updated to the last.
Unzip it and browse through the files, to familiarize yourself with those that come in a default installation.
Once you have visited them, access your server via FTP and look for suspicious files that are not the usual ones. The ones you find are probably malware.
The usual site is usually the /wp-content/directory.
The reason: You can easily delete the directories /wp-admin/ and /wp-includes/, and restore them with the clean copy just downloaded. So it is not interesting to infect these directories, because they are easily “cleanable”.
In /wp-content/, you can delete folders of plugins, and replace them with clean downloads as long as they are the same version!
Do you see how important it is to be updated?
Also Read – How To Disable Directory Browsing in WordPress Via .htaccess & Plugins
Check for malicious code on your server
Following the above logic, sometimes hackers do not infect WordPress files, but instead, infect or place files on your server directly.
They often use Iframes tags, to load remote sites, or an executable file type exe, cmd, etc. that infects the computer of your visits.
So pay attention to this code!
Search for example:
Hidden iframes: <iframe style = ”width: 0; height: 0;”> at the beginning of an html file.
Unintelligible code blocks:% wwww% yyy% zzz% /999/. This is usually encrypted code to hide malware so that you can remove it. Tools like Screaming Frog SEO Spider will help you find it.
Search in comments or areas that can be edited by users. Remember that using plugins like Akismet helps you reduce SPAM and infections.
Through the previous tool (Screaming Frog SEO Spider), look at the internal and external links, so you can find out where you are sending traffic and if there is a suspicious site.
Check your .htaccess file. It is the favorite site for hackers to redirect and add malicious code. Be sure to check it from the beginning to the end. Sometimes the malicious code is under hundreds of empty lines.
In the same case as the previous one, thoroughly check the wp-config.php file, especially after the line “Require_once (ABSPATH.’wp-settings.php ‘);”
Of course, check all the files that are downloadable on your website.
Delete the following files:
- /wp-includes/xmlrpc.php
- /wp-includes/css/css.php
- /wp-includes/css/style.php
- /wp-includes/js/jquery/jquery.js
- /wp-content/upd.php
- /wp-content/themes/[theme name]/temp/e9815adced6d3.php (or similar)
- /wp-admin/upd.php
- Delete all images, zip files or other files that are no longer needed
- Remove all unused plugins.
- Remove all unused WordPress themes.
Modify passwords
If we have completed the previous step, we must now do it again.
We will change the password for entering WordPress, cPanel, FTP, MySQL and any other place where we have used passwords.
We insist that we should get used to using strong passwords. For this, we can use some applications that will be responsible for remembering even the most complex and robust passwords (LastPass, 1Password, and Dashlane, among others).
We always recommend using strong passwords. You can read our article on how to change passwords in WordPress.
In addition, when we have many users we can force the reset of the passwords of all of them using plugins such as: Expire Passwords and Emergency Password Reset.
Request Google to review your site
This step is also covered under google blacklisting warning tutorial.
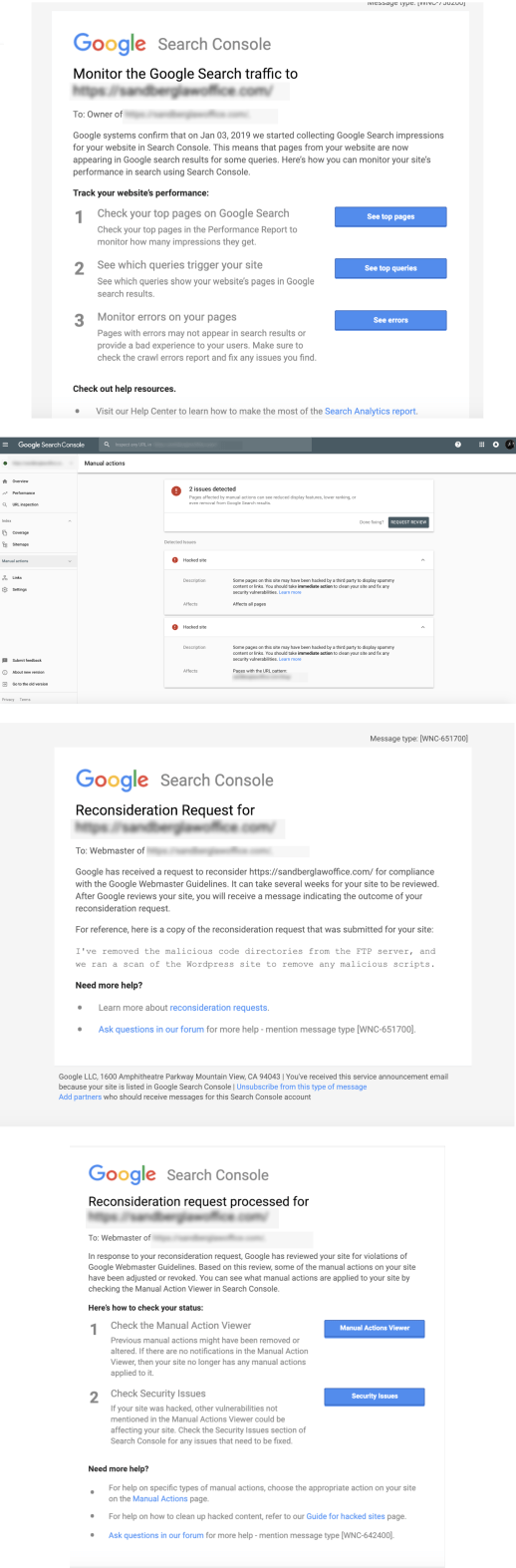
Google review ensures all the security issues are addressed before the site is reinstated.
Once you are sure that all malicious code (malware) has been removed, we return to Google Webmaster Tools to request a malicious software review of the site. Google will examine the site and, if it does not detect software of this type, will remove the warning label that appears on the entry of the search results page corresponding to that site.
Go to Google Search Console, then open the “Security Issues” report section and then request a review.
- On the Google Webmaster Tools home page, select the site.
- Click Diagnostics and then select Malicious Software.
- Click Request a review.
Once it is confirmed that your site is clean, it may take up to a day before the malicious software warning is removed from the site in the search results.
You can use our Request a google review template designed by our security experts that you can submit to the Google Search console team.
The review will not take long. If your website is free from infections, it will regain its SEO status within 24 hours after completion of the review.
These tips will help you to remove “This site may be hacked” Warning message from WordPress. If your issues are still unresolved you can talk to our experts!. We can solve “This Site May Be Hacked” problem, usually in much less than 24 hours, especially if your website is made in WordPress. So if your site is infected, even if you have the red screen and can no longer access it, contact WP Hacked Help team. We offer WordPress malware removal, and security audits by experts.
How to Prevent Being Suspended in the Future?
Indeed, you have successfully fixed the issue but there’s no guarantee that your site won’t be hacked again. As a WordPress site administrator, you can do a lot to improve the security posture of your site. You can avoid future attacks by taking preventive measures. This will ensure that your website remains protected from hackers, bots and the rest.
We could keep looking for clues and more clues very easily. And surely, if someone wants to access that website, these details will be the first ones they will look for.
To avoid this type of thing and improve the security of your WordPress, we will go through a series of very simple WordPress security tips, available to everyone, which will at least make things a little more difficult for the next thug that is posted on your website.
So without further delay, let’s do it.
Keep You Website Up-to-date
Earlier we spoke of how skipping wordpress security updates is a major reason behind why websites get hacked. This may seem obvious, but making sure you keep all software up to date is vital to keeping your site secure. This update applies to both the server operating system and the software you use on your websites, such as a CMS or a forum. When website security flaws are found in software, hackers are quick to try to abuse it.
If you use third-party software on your website, such as a CMS or a forum, you must ensure that you quickly apply the security patches. Most providers have a mailing list or RSS feed detailing the security issues on their website. WordPress and many other CMSs inform you of system updates available when you log in.
WordPress Site Maintenance
As we mentioned earlier, you must keep things updated on your site. Often, WordPress is able to automatically update itself when larger security issues detected, but leaving old versions of themes and plugins on your server is equally risky. Keep an eye on the available updates and apply them as soon as you can.
If you’re uploading anything by FTP, make sure you set up Correct file permissions for WordPress each time.
Note: Do not download premium themes and plugins from unofficial sites.
Also Read – WordPress site Maintenance Checklist
Switch to HTTPS
HTTPS is a protocol used to provide security on the Internet. HTTPS prevents man-in-the-middle type of attacks where a third-party entity sits between your visitor and your site to retrieve a copy of the information your visitors send to you (credit card number or credentials). If you have confidential information from your users, it is strongly recommended to use HTTPS.
HTTPS is also a good point for Google and therefore for your SEO. The search engine thus boosts the rankings of websites that use HTTPS. In addition, HTTP is about to disappear now is the time to update it to HTTPS!

Check your passwords / Use Stronger Credentials
Everyone knows that we have to use complex passwords, but that does not mean we always do it. It is crucial to use strong passwords for your server and the administration area of your website. It’s also important to emphasize good password practices for your users to protect the security of their accounts.
The WordPress login page is the most vulnerable page of your website. Hackers target that page and try to guess your usernames and passwords. Having a strong password and a unique username makes all the difference. And being an admin of the website, it’s your responsibility that all users of your website are using strong credentials. It also helps preventing brute force attacks. That is why you need to have a strong password policy in place. You can also use the passwordless login authentication method to login into WordPress website. This is most advance method and secure way to access your WordPress website.
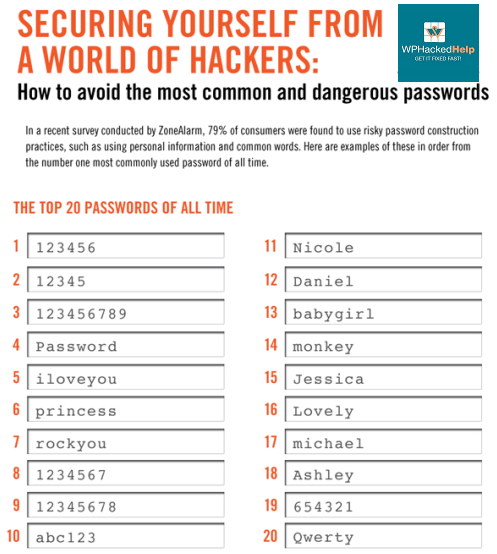
Hackers use different methods to try to access your accounts and those of your users. The most basic way is to manually type letters, numbers and symbols to guess your password. The most advanced method is to use what is called a “brute force attack”. In this technique, a computer program scans through all possible combinations of letters, numbers, and symbols as quickly as possible to break your password.
- The longer and more complex your password, the longer it takes.
- Three-character passwords take less than a second to crack.
- Long passwords are the best.
- The more they include words or phrases with no particular meaning, the better they are.
- Combinations of letters that are not in the dictionary, unfamiliar expressions or bad grammar are the most difficult to crack.
- Also, do not use sequential characters on a keyboard, such as numbers in order or the widely used “azerty”. Randomly mix symbols and numbers with letters.
- You can substitute a zero for the letter O or @ for the letter A, for example.
Use unique passwords for each account. When hackers engage in large-scale hackers, they gain access to lists of email addresses and passwords. If your email account has the same password as other sites, your information can be easily used by hackers.
Finally, think about double authentication. Two passwords secure better than one! Remember to Setup WordPress Two-Factor Authentication
Beware of error messages
Pay attention to the amount of information you have received through your error messages. Provide only minimal errors to your users, to make sure they do not disclose the secrets on your server (for example, API keys or database passwords).
Do not provide full details about exceptions either, because they can make complex attacks like SQL injection. Keep detailed errors in your server logs and show users only the information they need.
Most Common Error Messages Includes:
- How to Fix Pluggable.php File Errors in WordPress?
- How To Fix WordPress Upload Failed To Write File To Disk Error?
- WordPress HTTP Image Upload Error
- 503 Service Unavailable Error in WordPress site
- Parse Error: Syntax Error Unexpected in WordPress
- “This Account Has Been Suspended” WordPress
- WordPress Not Sending Email
- Sorry, This File Type Is Not Permitted For Security Reasons
- Error Establishing a Database Connection in WordPress
Avoid file downloads
Allowing users to upload files to your website can pose a great risk to the security of your website. The risk is that any downloaded file, as innocent as it may seem, may contain a script that, once executed on your server, completely opens your website.
If you allow users to upload images, you cannot rely on the file extension or MIME type to verify that the file is an image because they can easily be falsified. Even opening the file and reading the header, or using functions to check the image size are not foolproof. Most image formats allow you to store a comment section that could contain PHP code that could be executed by the server.
Use Website/Content monitoring tools
Content monitoring tools help you track and monitor changes on any website under consideration so you can take immediate actions as you like.
Get vital info on external posts, Monitor, track and archive website changes. You can easily Compare visual, text, keyword, image and HTML change history and get detailed alerts. Such tools would help you track and monitor the content and will send you a notification each time the content has changed. For this purpose, here are 5 of the best content monitoring tools that notify you of any changes in your favorite pages.
Install a Security Plugin
Having a best wordpress security plugin is the best way to ensure that your website is protected 24×7. The security plugin will run a daily scan on your website and clean it if it’s infected with malware. Most security plugins offer firewalls that’ll help thwart attacks launched on your site. Security plugin like Jetpack, SecuPress, BulletProof Security offers advanced measures that help harden your website against hack attempts.
Google’s Search Console Alert
Although the site is virus-free, the red screen warning may still appear. To get rid of it, what is appropriate is to ask Google for reconsideration. The procedure is next:
- Visit Google Search Console enter your Google account. Once in the center, enter the site address and press the ” Add a property ” button.
- Google requests verification of site ownership. One way to do this is to download an HTML document to the computer.
- Upload the document to the server, to the directory where WordPress is installed (usually it is the public_html folder).
- Go back to Google Search Console and press the “Verify” button. If the procedure was successful, Google sends you a success message.
Of course, these steps, although simple, require time and more time, depending on the type of the website, the traffic you receive and similar variables, it is the least one has because we want everything to return to normal as soon as possible. You also can set up for Google Alerts on your site to get notifications about any suspicious results for your site.
Check Google Index/Crawling Time to time
Sometimes, hacker blocks Googlebot from indexing your website online. So, not being indexed by Google can plummet your traffic and thus growth of your business. Make sure Googlebot is not blocked on your website by adding website on Google Search Console & Configuring robots.txt file in Google
CHECK OUT DETAILED WP GUIDES:
- WordPress Security – A Step by Step Guide
- WordPress Malware Removal Checklist
- WordPress Theme Security Guide


